Install an Agent on your Kubernetes Cluster
Prerequisites
-
Kuberentes cluster - can be any cluster, including on your on-premise network. Please note that Torque does not support cluster nodes on ARM architecture.
-
Outbound Ports for Kubernetes Cluster Nodes must be open to allow Torque to access and communicate with the cluster.
-
Command-line with kubectl installed connected to your cluster. To connect to the cluster use:
kubectl config use-context <your-cluster>For further reading on connecting to clusters hosted on your cloud, check these links: EKS, AKS, GKE.
-
One or more target namespaces on the cluster where the Torque agent will create resources.
-
Authentication and permissions - The agent will need sufficient permissions to create the environment's cloud resources. There are a couple of ways to provide the permissions, depending on where the environment resources will be created.
-
To create K8s resources (Pods, services, secrets... etc.) using K8s manifests or helm charts, create a service account with sufficient permissions to create the K8s resources. For Example:
Let's say that you would like to deploy your environments into a namespace called "my-ns". Use the below commands (change to your real namespace name) to create the appropriate service-account:
kubectl create serviceaccount my-ns-edit-sa --namespace=my-nskubectl create rolebinding my-sa-edit-rb --clusterrole=edit --serviceaccount=my-ns:my-ns-edit-sa --namespace=my-ns -
To create resources on your cloud using Terraform:
- If your cluster is an EKS (resources will be created on AWS):
- (Recommended) Create a designated service account annotated with an AWS role. See Terraform Authentication on EKS for details. Or,
- Ensure that the Cluster service role has sufficient permissions to create the environment.
- If your cluster is an AKS (resources will be created on Azure): Provide the account's authentication credentials when creating the agent in Torque. For details, see Terraform Authentication on AKS.
- If your cluster is a GKE (resources will be created on GCP), see Terraform GKE Authentication.
- For other types of clusters, or if you want to connect to your AWS/Azure with your basic credentials, there is no built-in authentication with Torque so there are no pre-requisites related to authentication and permissions. You can store your cloud credentials in the Torque secret store and use them for your TF deployment.
- If your cluster is an EKS (resources will be created on AWS):
-
Setup
- In Torque's Administration page, open the Cloud Accounts tab.
- Click Connect a Cloud.
- Select the cloud provider and the type of Kubernetes to use, and give the agent a name.
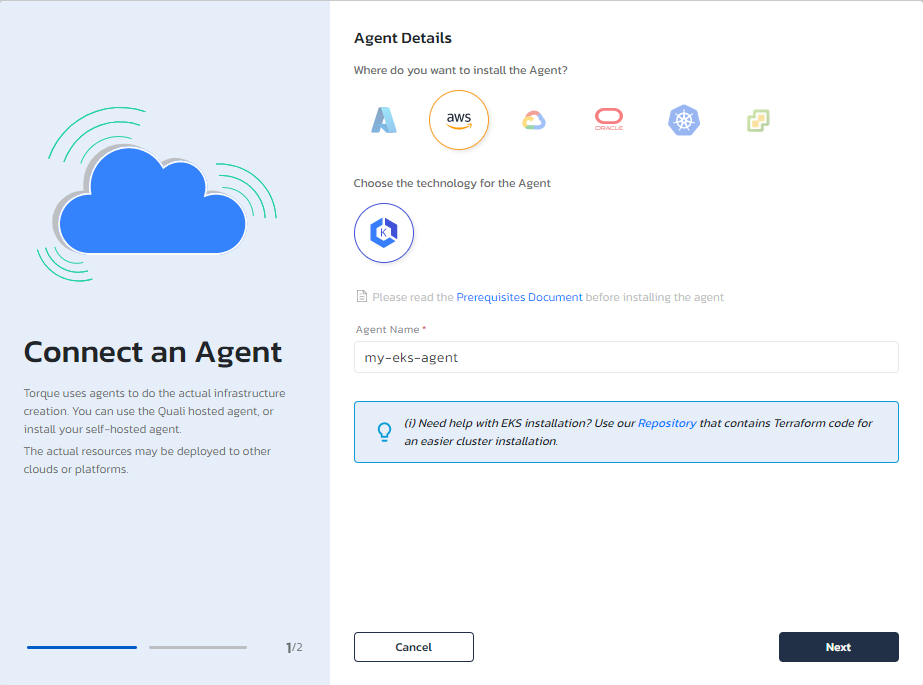
- Click Next.
- Click Generate and copy the command that is displayed
- Paste the command in your command-line window to deploy the agent to your cluster. For example:
kubectl apply -f https://portal.qtorque.io/api/settings/executionhosts/deployment/k***roi/deployment.yaml - A Connected! status is displayed in Torque, indicating that the agent was successfully installed and can communicate with Torque.
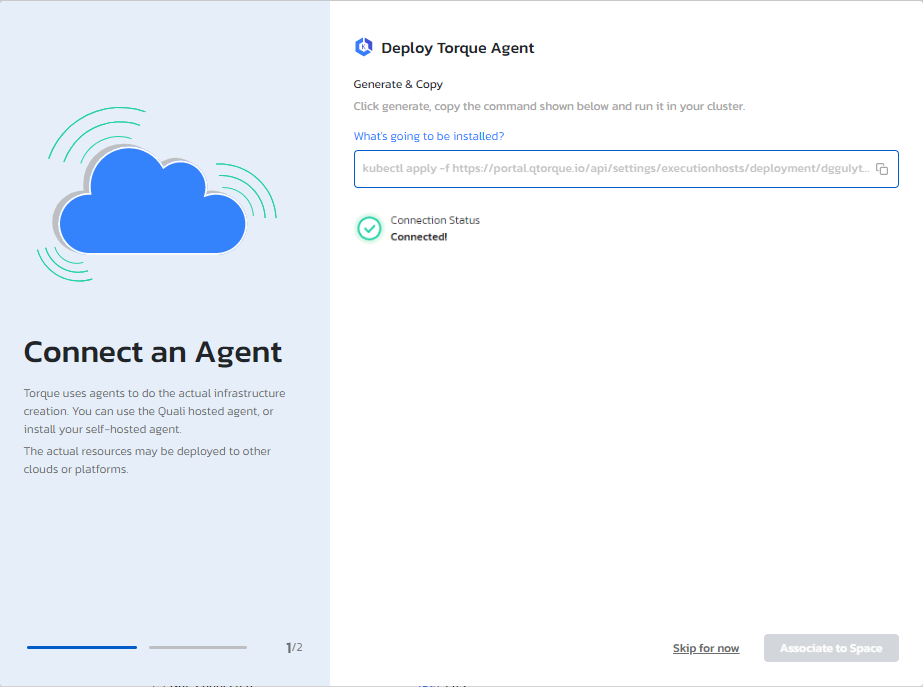
- Click Associate to Space to connect the host to a space, and provide the details you obtained in the prerequisites section.
Troubleshooting
If the agent fails to connect with Torque, you can try the following to identify the problem.
Replace the "agent-namespace" with your agent's namespace. You can find it in:
Administration --> Agents --> Identify your agent --> Click on the 3 dots menu --> Edit Agent --> Advanced K8s settings:
- Make sure the agent pod is running and healthy. You can run the following command on your cluster:
kubectl get pods -n <agent-namespace> -l app=torque-agent - Make sure outbound http connection to Torque is open:
and also
kubectl exec -it $(kubectl get pods -n <agent-namespace> | grep torque-agent | awk '/'$2'/ {print $1;exit}') -n <agent-namespace> -- /bin/sh -c "curl -v http://portal.qtorque.io/hub/agent";kubectl exec -it $(kubectl get pods -n <agent-namespace> | grep torque-agent | awk '/'$2'/ {print $1;exit}') -n <agent-namespace> -- /bin/sh -c "nmap -p 5671 acrobatic-lime-gerbil.rmq3.cloudamqp.com"; - Check the agent pod logs. You can run the following command:
kubectl logs $(kubectl get pods -n <agent-namespace> | grep torque-agent | awk '/'$2'/ {print $1;exit}') -n <agent-namespace>